Domino 5.0: Securely store credentials to support compliance requirements
Elliott Whiting2022-02-16 | 4 min read
Introducing the Secret Store in Domino 5.0
Domino is constantly innovating to make our Enterprise MLOps platform as secure as possible. One of the most basic ways that we do that is by making sure your data is only accessible by those who should have access. Even administrators, who need access to the entire platform, should not be able to access specific data. This is especially important since many of our customers work in regulated industries and their data storage has to be compliant with standards such as FIPS, HIPAA, and PCI. With all of this in mind, Domino has introduced a Secret Store to encrypt sensitive data at rest and help ensure that organizations can comply with security standards.
Domino now stores sensitive user data, including credentials, API keys, and the new data source access secrets in a secure Secret Store, using HashiCorp Vault. Data stored in the Secret Store is encrypted at rest and – if you have Istio enabled in your Kubernetes cluster – connections to it are secured with TLS.
The Secret Store in Domino provides security teams the ability to produce a log of secrets that have been accessed, and then revoke those secrets if there is suspicious activity – or worse, a full security breach. Your security engineers will sleep better at night, even if your organization is not in a regulated industry.
How it works
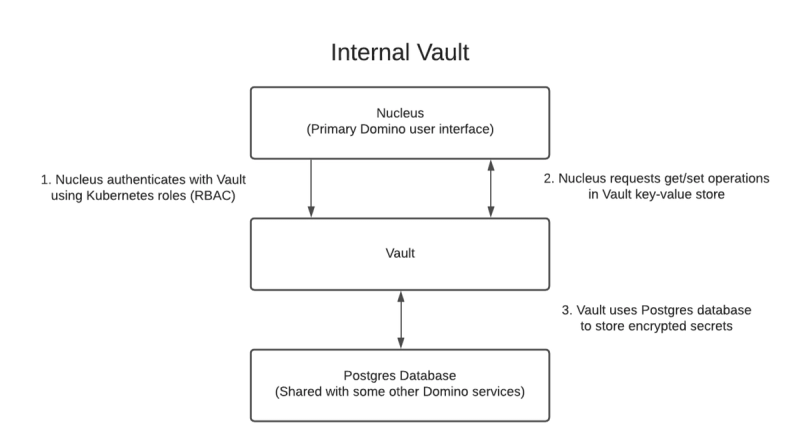
New installations of Domino will deploy a pre-configured instance of HashiCorp Vault to your Kubernetes cluster. The Nucleus service (the main Domino user interface) then authenticates against the Vault service and is authorized to read and write key-value pairs in the Vault.
However, many organizations already have a Vault installation and don’t want to manage a second service. Other organizations may have not deployed a Vault yet, but want the flexibility to integrate an installation with an existing HSM and PKI infrastructure and define their own policies. In both cases, Domino can be configured to use an external Vault instead, using the organization’s existing encryption and key rotation policies. Domino can then access an external Vault instance via literal token authentication or token path authentication.
The screens in Domino to create user environment variables, API keys, etc., are the same as before, but the infrastructure changes behind the scenes simply change where your data goes once you have submitted it.
For example, to set a user environment variable, go into “Account Settings” in your user menu in the bottom left of the Domino UI.
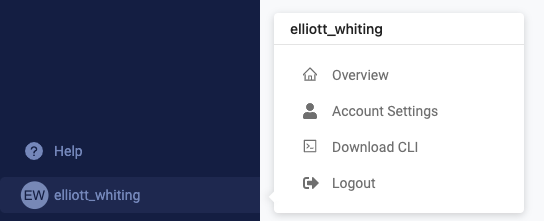
Under the “User environment variables” section, add the key and value for your new environment variable and click “Set variable”. This process should look familiar to both current Domino users and users of many other products in DevOps and beyond.
Once you click “Set variable”, Domino’s Nucleus service will write the key-value pair to the Secret Store and the pair is kept encrypted in its database. When you need to reference your environment variable in a project, Domino reverses the process, reads the key-value pair from the Secret Store and inserts the value into your project. From the user’s point of view, the process is simple because all the hard work is done for them.
Conclusion
Domino Data Lab is excited to introduce the Secret Store to Domino – it extends the security measures already in place in Domino and simplifies compliance with company policies and industry standards. Upgrade to Domino 5.0 and you’ll get a pre-configured instance that you can start saving secrets to immediately. And for organizations that need more flexibility, Domino can connect to existing instances that comply with established policies. Either way, Domino is ready to help all organizations meet the most stringent security standards.
Domino is the Enterprise MLOps platform that seamlessly integrates code-driven model development, deployment, and monitoring to support rapid iteration and optimal model performance so companies can be certain to achieve maximum value from their data science models.
Elliott Whiting is a Field Engineer in the EMEA region for Domino Data Lab. He has a wide range of experience in DevOps and system administration. Longer ago than he’d like to admit, he majored in three European languages, so working with customers around the EMEA region gives him lots of opportunities to use all of these skills.



